Security Operations
Stay secure with 24×7 reactive and preventive actions by a team that knows YOU

Security incident at 2am.
Who’s there to react?

Got the vulnerability scan report,
it’s 70 pages. Now what?

When the consultant leaves,
who will manage all these tools?
Set up a security operations platform
Security tools are essential, but they come and go. Start with a deep understanding of existing infrastructure, user characteristics, desired security posture and limits on budget. Craft a security solution suite with zero lock in and no proprietary tools. Then tune and operate to get the true value from the platform.

24×7 security incident response
Stratogent is tool agnostic. Whichever EDR or MDR service emits the alarms, we catch the ball as your INSIDE Incident Response Team.
We learn your custom procedures and analyze volume trends to automate as much as is pragmatic.
Threat response and MDR operations
Screening of inbound notifications from in-house or external threat detection service. Containment of incidents per set SLAs and ‘run the problem to the ground’ with root cause analysis and permanent remediation. To avoid 3rd party lock in, the rules are encoded in SOAR automation engine and not in the 3rd party service.
SIEM operations
Have us interface with embedded SIEMs in MDR services or manage and maintain standalone SIEMs.
Anti malware and EDR operations
Containment, removal, reimaging, scanning and any others steps necessary to ensure a clean and safe system.
Email security
The number one threat vector for business today is email compromise. Have us manage the anti-spam solution, stop account takeovers and run internal phishing campaigns for awareness training. We will work with your end users to keep them safe.
Network IDS operations
The extended network across offices, clouds and remote users is vital to protect. We will notify about abnormalities specific to you and proactively initiate reactions and remediations.
Preventive security
IT needs to get ahead with proactive security and prevention of compromise. Nowadays the C suite asks us what IT is doing to protect the company’s business.
Bugs and misconfigurations are the norm in complex enterprise IT solutions, so it is essential to address vulnerabilities and privileged access, not once but ALL the time.
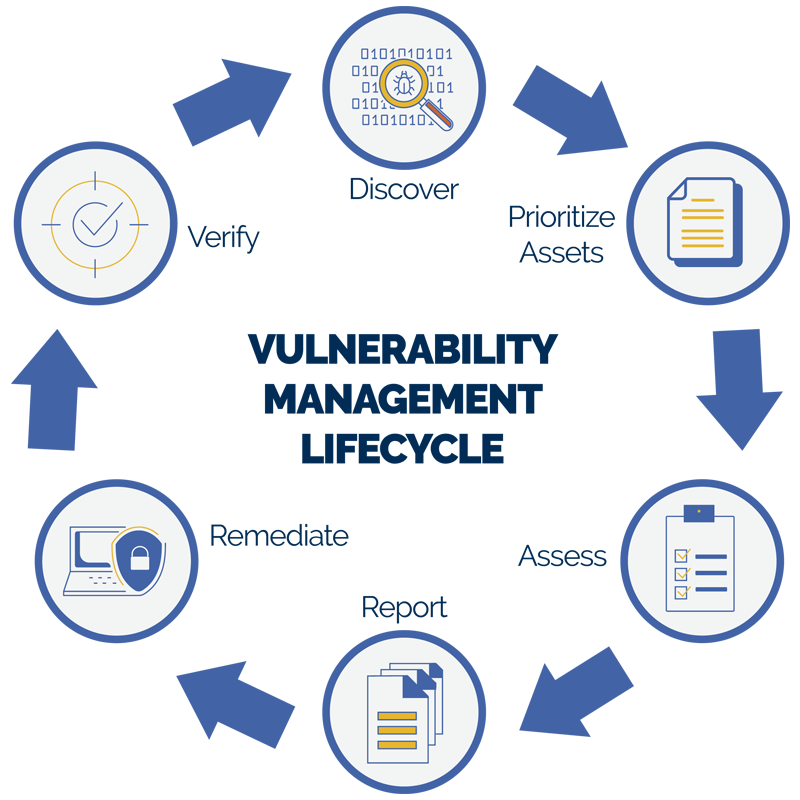
Continuous triage of scan reports
Our team is aware of your network, systems and cloud apps. Risk based prioritization of what to remediate is key.
Regular remediation cycles
This is the part that matters and takes time to carefully analyze the patch or configuration fix, run through change control, rollout across the environment and ensure each vulnerability is indeed addressed.
Privileged access management
Safe vaulting of secrets, periodic user access reviews, regular rotation of credentials keep you safe.
Meaningful reports
The proof is in the pudding… er, reporting. With useful graphs, the right metrics and KPIs we make IT look good!
